For a guy working in the field of security, publicly open computers such as Kiosks, are always very attractive to start playing around with. It is hard to ignore them. In public areas such as shops, hotels and airports those systems are located everywhere. The functions of the public available computers vary such as displaying information, ordering things, printing tickets and even paying your groceries.
We performed multiple penetration tests on these kinds of systems. In a lot of situations, it is possible to perform actions on the device which could lead to compromising the system. If an attacker succeeds compromising such a device, the following risks are among most common and impactful:
KPN Security tested multiple systems with different functionalities. A key component when attacking such a system is playing around with input. All input to such a device, can be possible an entrance for an attacker. Be creative, input is very broad, for example:
Usually public systems are running an interface that limits the user to only perform the actions that are actually allowed. One of the first goals an attacker usually likes to accomplish, is to escape this interface to get other functionalities of the underlying operating system, such as Windows, available.
Some real life attacks
One of the first steps is probably using the keyboard if connected or the touch screen of the device. Try to find clicks, keys or key combinations to trigger unexpected behavior on the Kiosk (e.g. ALT+F4, CTRL+ALT+DEL etc). In some situations, the results of those combinations are surprisingly effective and operating systems functionalities appear. Sometimes, the brute forcing technique is even effective, however this is a bit too enthusiastic:

Keyboard
If you are lucky there is already a keyboard connected. Sometimes, there is no keyboard connected, but USB interface are available (USB, USB-C, Micro-USB etc). Try to connect your own keyboard, using converters where needed.
We have found keyboard attacks to work out on Kiosks. To create a proof of concept, we created Rubber Ducky devices and a Kali NetHunter phone to show the impact. We were able to create a pretty cool proof of concept video, which showed that we were able to compromise the Kiosk within 30 seconds after plugging in a Rubber Ducky or a malicious Nexus 5 phone.
After our proof of concept, which used special keys like ALT and CTRL, those keys were blocked by the developers. One of my colleagues created another cool attack on the administration panel. A pincode was required in order to gain access to the administration panel of the Kiosk. He built a pincode bruteforcer with the Rubber Ducky, because integers (0-9) were not blocked by the system. This allowed him to obtain the administration pincode in a limited amount of time.
Touch screen
The picture below shows escaping to cmd.exe on a touchscreen information display. We were able to popup Windows menu's by holding down the mouse on specific locations of the touch screen, which resulted in a Windows right-click menu to pop up. By using the Windows menu and other Windows functionalities, we were able to get an on-screen keyboard and a command prompt.
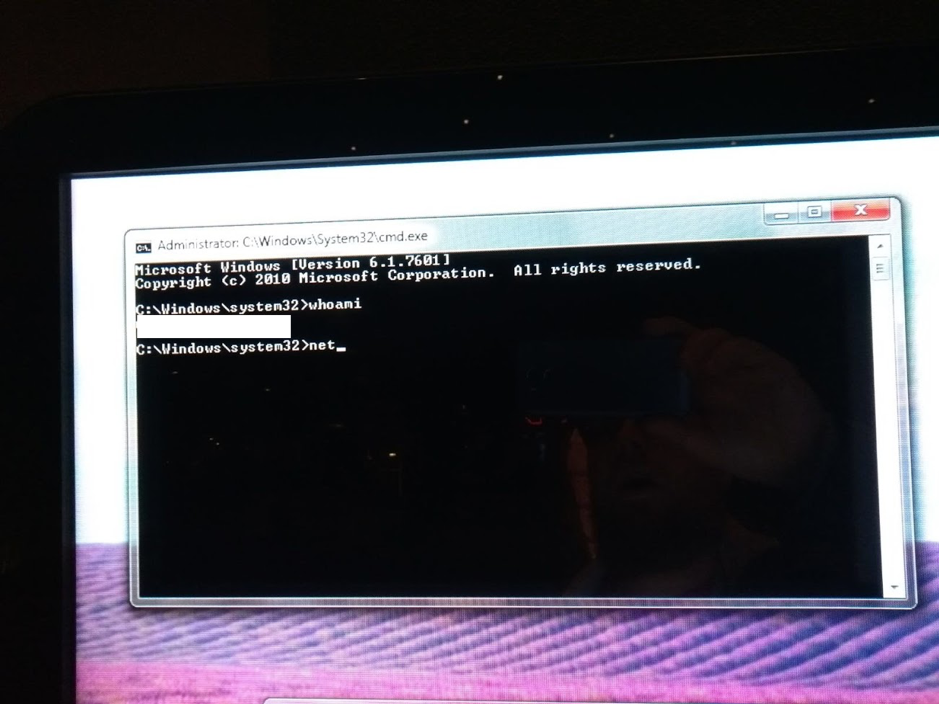
Figure 1 The final goal is usually to obtain a command shell / powershell, as this usually gives full control over the system.
Barcode scanner
Sometimes the attempts through the keyboard or touch screen are not working out, and the system is not performing any strange behavior which would be an indication of escaping the interface. In that situation, an attacker could look for other input possibilities into the device. For example, a barcode scanner is a frequently seen device on a public system. This allows users to scan products, tickets, etc.
Barcode scanners are from an attacker perspective interesting attacks vectors. In most situations, a barcode scanner is nothing more than a keyboard device. By scanning a malicious barcode, an attacker might succeed in sending keyboard commands to escape the interface. This attack is called, "bad barcode". We have seen this attack working multiple times on public systems, because a developer usually does not realize that the operating systems interpreters the device as a keyboard.
Source: @tombkeeper
Ethernet interface
Another public system that the KPN Security departement hacked, was their own coffee machine. It had a public ethernet interface available. After plugging a UTP cable into the machine, a SQLite database was available. By replacing some values it was possible to modify the coffeee machines images and text:
Above attacks are a couple of examples. Many different public systems use their own 'application whitelisting' implementation. In the past, in a lot of situations, the implementation was 'just' an application running on a regular Windows computer, while attempting to block / prevent execution of malicious actions that might be performed by its users.
Windows 10 introduced assigned access
The issue from above approach, is that the developer needs to block every malicious action that might be performed by an attacker. He needs to predict every possible action and prevent it to happen in the correct way. Almost an impossible task, as a regular Windows machine contains so much functionality.
Since Windows 10 Microsoft introduced an awesome feature, called Kiosk mode or Assigned Access . This is a built-in Windows feature to run an application above a lock screen. This is a great feature for preventing attacks, because if an attacker succeeds in escaping the Kiosk interface, he still gets the default Windows 10 lock screen.
Conclusion
In this article we have demonstrated some of the different attack methods to attack public systems / Kiosks. However, this is a subset of all the different possibilities. We have seen quite some vulnerable systems in public spaces. How can we defend these systems?
Use new Kiosk mode features such as assigned access when building a new application. This feature has been provided by Microsoft to increase the security of such a system. Trying to block / prevent malicious action by blocking (blacklisting) instead, has a high chance to fail.
Consider the machine to be untrusted and that the machine will be compromised. Limit storing sensitive information to the absolute minimum, also in terms of duration. The network behind the system is important. Use segmentation to prevent that the Kiosk connects to any other systems within the internal network. Otherwise, the Kiosk might be used as a stepping stone to further compromise the organization / network. Segmentation can quite easily prevent this worst-case scenario from happening.